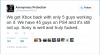
http://www.dailydot.com/technology/lizard-squad-hackers/
Some tier 1 isp routers have been hacked and used to send traffic of 1.2 terabits per second.
That is not correct, the size of the DDoS is claimed to be 1.2 Terabits.
They claim to have hacked some routers and core network components.
I have not seen anything about what kind of DDoS attack this is, but to create a 1.2 terabits you have quite a big botnet or something that really amplifies.
BoardBonobo mentioned in another thread about some google maps plugin for WP/Drupal that might be a source.
Looking at akamai for DDoS attack types, most of it is SSDP (UPnP) and then NTP etc.
http://www.stateoftheinternet.com/t...al-ddos-attack-sources-types-and-targets.html
Speculating wildly, based on that article in the dailydot and the akamai info, I would guess that they are doing multiple types at the same time.
And stretching even further, by believing that they have hacked core network equipment close to Sony and MS. I would guess that they are doing snmp amplification attacks with local network equipment where MS & Sony servers are located.
This has a twofold reaction, the servers gets a lot of extra traffic and the routers/switches also get bogged down with collecting and sending the data to the servers. Ie you saturate the links going to the servers and slow down the network equipment by taxing the cpu with extra work.
IMHO the only, if any, sophistication in this attack, is the coordination of multiple attack types if that is what is going on....
And the line about big enough budget, well anybody can do anything with big enough budget.
My solution would be to put up a big reward so that somebody would inform on their best friend and then send spec ops team to kill them as a deterent for the next group that wants to do this.
Might not be very feasible, but if they can ask for big enough budget, I can add any means is fair

Now please let me login to PSN so I can upgrade gjallarhorn