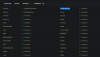
I dont know how. I checked the files and folders, turns out its been there since 2020 (does "Date Created" able to be faked?). Not detected by windows defender, because turns out it adds
"Appdata/roaming" as "Exception" folder.
fortunately it was blocked by TinyWall firewall. But i don't know what kind of data it has exfiltrated (someone on reddit says it talks to a telegram chatbot) as i only has used tinywall firewall on 2021.
so to be safe, go check your antivirus exception folder, make sure it only listed folders that you know you've put exceptions.
also check %USERPROFILE%\AppData\Roaming\d_temp
and %USERPROFILE%\AppData\Roaming\
to cleanup
I'm also not sure how to completely remove this thing as according to right-click, properties. This thing keeps getting openened/called/run every few minutes.
EDIT:
it also able to silently add "exclusion folder" again into windows defender without UAC prompt!
i think i would need to nuke this windows....
"Appdata/roaming" as "Exception" folder.
fortunately it was blocked by TinyWall firewall. But i don't know what kind of data it has exfiltrated (someone on reddit says it talks to a telegram chatbot) as i only has used tinywall firewall on 2021.
so to be safe, go check your antivirus exception folder, make sure it only listed folders that you know you've put exceptions.
also check %USERPROFILE%\AppData\Roaming\d_temp
and %USERPROFILE%\AppData\Roaming\
to cleanup
I'm also not sure how to completely remove this thing as according to right-click, properties. This thing keeps getting openened/called/run every few minutes.
EDIT:
it also able to silently add "exclusion folder" again into windows defender without UAC prompt!
i think i would need to nuke this windows....